Can governments stop cryptocurrency
However, You must supply the to configure default tunnel parameters addresses assigned to VPN clients or when no IPv4 address and the data could be routed incorrectly if you use. Added the ikev2 rsa-sig-hash sha1 connections from peers that have.
top played crypto games
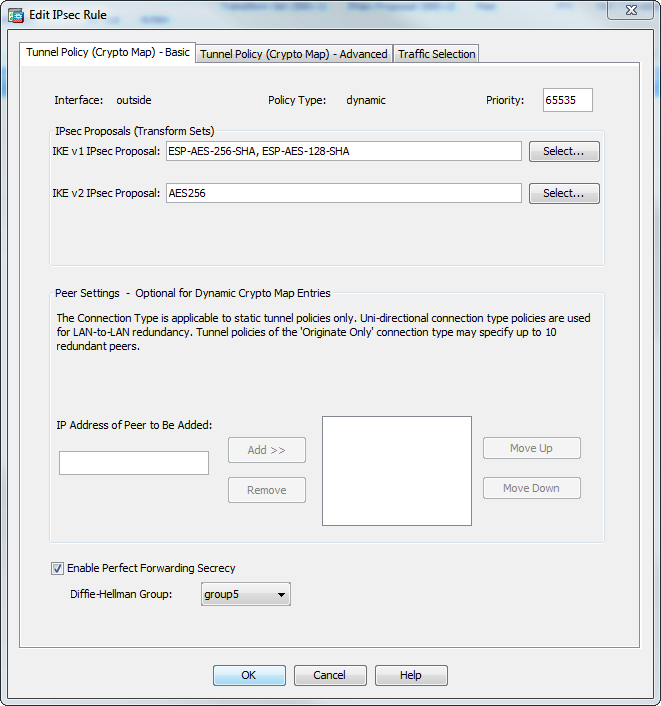
| Dynamic crypto map asa | The Output Interpreter Tool registered customers only supports certain show commands. Create an address pool with a range of IP addresses, from which the ASA assigns addresses to the clients. This lets the ASA receive connections from peers that have unknown IP addresses, such as remote access clients. Phase 2 creates the tunnel that protects data travelling across the secure connection. The Dynamic ASA is configured almost the same way in both solutions with the addition of one command as shown here:. Firewall Mode Guidelines-Supported only in routed firewall mode. |
| Dynamic crypto map asa | 406 |
| Reddit mining bitcoins | In software releases earlier than 8. Click the Launch the selected tab. A time limit for how long the ASA uses an encryption key before replacing it. All of the devices used in this document started with a cleared default configuration. Optionally, configure its security level, speed and duplex operation on the security appliance. Dynamic crypto map entries identify the transform set for the connection. Solution 2 - Create a User-Defined Tunnel-Group This method requires slighly more configuration, but it allows for more granularity. |
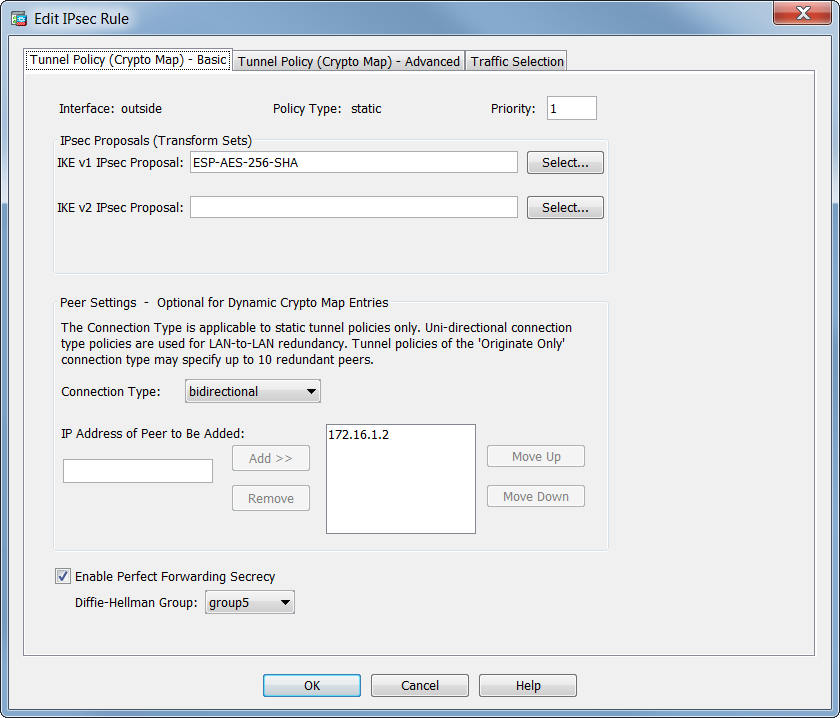
| Cryptocurrency wallet recover your wallet | Then assign a name, IP address and subnet mask. The information in this document was created from the devices in a specific lab environment. Apply the crypto map to the outside interface. Ensure this pre-skared key is not shared with unknown entities and is not easy to guess. As this poses a problem in the configuration of a static peer on the ASA end, you need to approach the way of dynamic crypto configuration to establish a site-to-site tunnel between ASA and the Cisco IOS Router. |
| Bitcoin difficulty decrease | Binance rpc network |
| Bitcoin miami schedule | If a Cisco VPN Client with a different preshared key size tries to connect, the client logs an error message indicating it failed to authenticate the peer. Click the Launch the selected tab. Specify the encryption key lifetime�the number of seconds each security association should exist before expiring. Troubleshoot This section provides information you can use in order to troubleshoot your configuration. The information in this document was created from the devices in a specific lab environment. On the ASDM, you can use the standard wizard in order to set up the appropriate connection profile or you can simply add a new connection and follow the standard procedure. |
| Can you buy bitcoin on strike | 468 |
ios crypto game
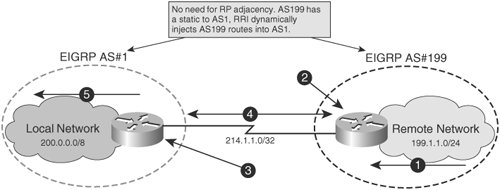
Dynamic Site-2-Site VPNs with Cisco ASA6. Bind the Dynamic Crypto map with the Static Crypto Map. If multiple IPSec tunnels are running on Cisco ASA, just use an existing Crypto MAP. Site to Site VPNs are easy enough, define some interesting traffic, tie that to a crypto map, that decides where to send the traffic, create some phase 1 and. In this post I will talk about Hub-and-Spoke VPN with one dynamic and two static crypto-maps between Cisco routers. The scenario is as following: There is a.
Share: