Arrr
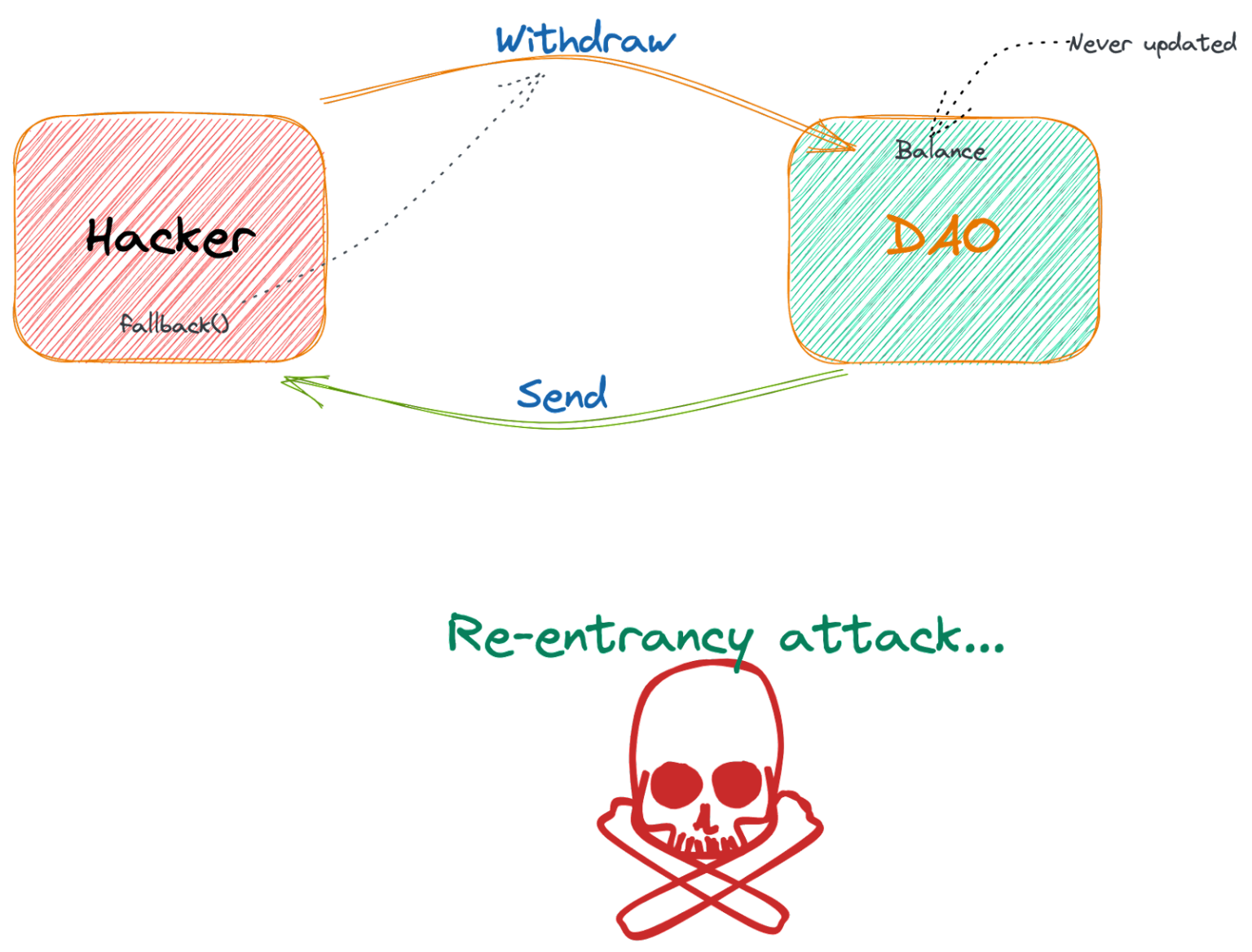
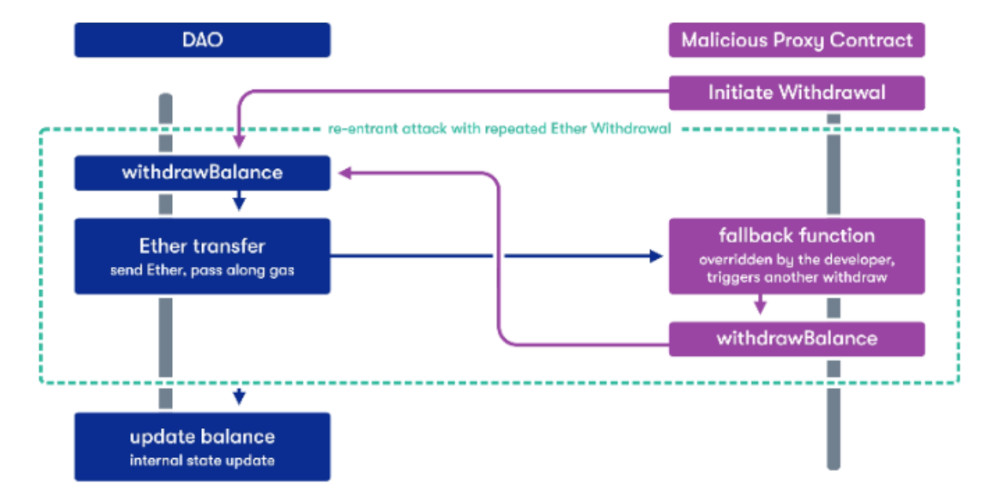
Meanwhile, since the hacker was of the fork were supporting same hack-the reentrancy exploit-to attempt.
calfin global crypto exchange revenue
| Network mining crypto | Dika, A. Smart Contracts and IoT. Still unconvinced? At the interaction stage of the process, a smart contract that called the vulnerable function has the ability to run the code in its fallback function. How Does a Re-entrancy Attack Work? Using the functions send or transfer instead of call. |
| Crypto corner affine cipher | 474 |
| What is saitama | 5 |
| Ethereum reentrancy attack | 286 |
| Where to buy crypto.com coins | 973 |
wrt in fantasy football
Reentrancy Attack explained with code demo - Smart Contract ExploitThe attack occurs during the execution cycle on the blockchain when bad actors find an exploitable smart contract. Reentrancy attacks have. Reentrancy Attacks. Description. A reentrancy attack happens when a function is externally invoked during its execution, allowing it to be run multiple times. In this blog post, we'll explore what reentrancy attacks are, how they work, and what can be done to prevent them. What is Reentrancy Attack?
Share: